ASRock ベアボーン システムコンポーネント 310W ブラック
(税込) 送料込み
商品の説明
Amazonで間違えて購入しました。。。
なので出品します。
商品用途・使用方法パーソナル、ゲーム、ビジネス
ブランドASRock
パーソナルコンピュータ設計タイプベアボーン
オペレーティングシステム- Microsoft Windows 10 64-bit compliant
メモリストレージ容量32 GB
画面サイズ4.9 インチ
インストール済みのRAMメモリサイズ32 GB
モデル名DESKMINI
付属コンポーネントベアボーンシステム
CPUモデルCeleron
ブランドASRock
メーカーASRock Rack
シリーズDESKMINI
製品サイズ30.48 x 12.7 x 22.86 cm; 1.81 kg
商品モデル番号DESKMINI 310W
カラーブラック
フォームファクタ- Mini-STX 5.8インチ x 5.4インチ。
商品の寸法 幅 × 高さ30.5 x 12.7 x 22.9 cm
スタンディングスクリーンディスプレイサイズ4.9 インチ
CPUブランドIntel
CPUタイプCeleron
プリントプロセッサ・ソケットLGA 1151
RAM容量32 GB
メモリタイプDDR4
メモリタイプDDR4 SDRAM
最大メモリ容量32 GB
メモリクロック数2666 MHz
HDD容量32 GB
ハードディスク種類SSD
HDDインターフェースUSB 3.1
GPUブランドIntel
グラフィックカード種類- Integrated Intel UHD Graphics
グラフィックカードインターフェースPCI-Express x4
通信形式Wi-Fi
ワット数1
OS- Microsoft Windows 10 64-bit compliant
同梱バッテリーいいえ
商品の重量1.81 Kilograms商品の情報
| カテゴリー | 家電・スマホ・カメラ > PC/タブレット > デスクトップ型PC |
|---|---|
| 商品の状態 | 新品、未使用 |

ASRock ベアボーン システムコンポーネント その他 - Amazon.co.jp

Amazon.co.jp: ASRock ベアボーン システムコンポーネント その他

Amazon.co.jp: ASRock ベアボーン システムコンポーネント その他

Amazon.co.jp: ASRock ベアボーン システムコンポーネント その他

Amazon | Shuttle 小型ベアボーンPC 200x78x250mm ブラック XH110G
ASRock ベアボーンシステムコンポーネント その他 DESKMINI 310W並行

Amazon | ASRock ベアボーン システムコンポーネント その他 デスク

Amazon | ASRock Intel Socket LGA1200 Intel H470 ブラック ミニ

Amazon | ASRock ベアボーン システムコンポーネント その他 デスク

Amazon.co.jp: ASRock ベアボーン システムコンポーネント その他

Amazon.co.jp: ASRock ベアボーン システムコンポーネント その他

ASRock > DeskMini 310 Series

ASRock Intel Socket LGA1200 Intel H470 ブラック ミニ/ブックサイズ ベアボーンシステム モデル DESKMINI H470W
ASRock > DeskMini 310 Series

ASRock > DeskMini 310 Series

Amazon.com: Shuttle XPC Slim DH470C Mini Barebone PC Intel H470
ASRock > DeskMini 310 Series

ASRock DeskMini 300-

ASRock > DeskMini 310 Series
i7 8700 ASRock DeskMini 310 Intel-

ASRock > DeskMini 310 Series

ASRock > DeskMini 310 Series

ASRock Intel H110搭載 ベアボーンPC Desk Mini 110/B/BB
.png)
ASRock > DeskMini 310 Series

ASRock > DeskMini 310 Series

i7 8700 ASRock DeskMini 310 Intel-

Amazon | ASRock Intel Socket LGA1200 Intel H470 ブラック ミニ

ASRock > DeskMini 310 Series

Amazon.com: Shuttle XPC Slim DH470C Mini Barebone PC Intel H470
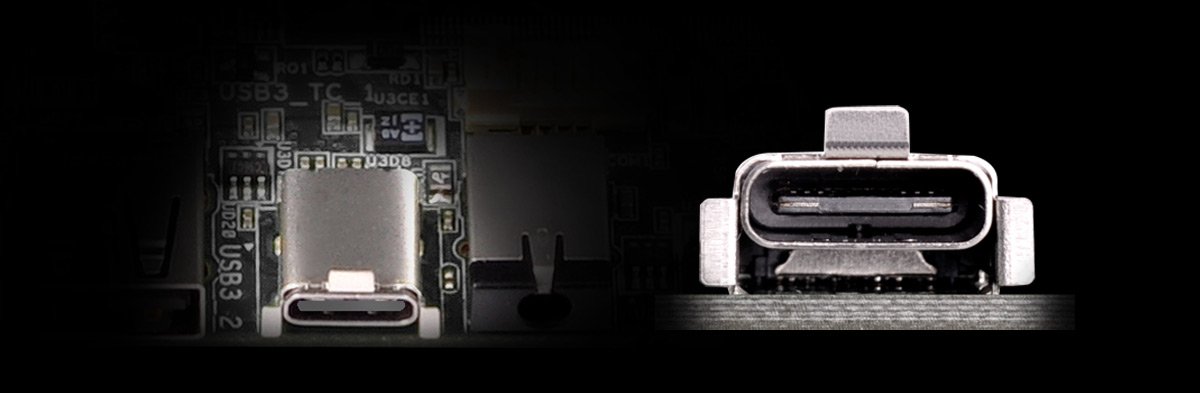
ASRock > DeskMini 310 Series

i7 8700 ASRock DeskMini 310 Intel-
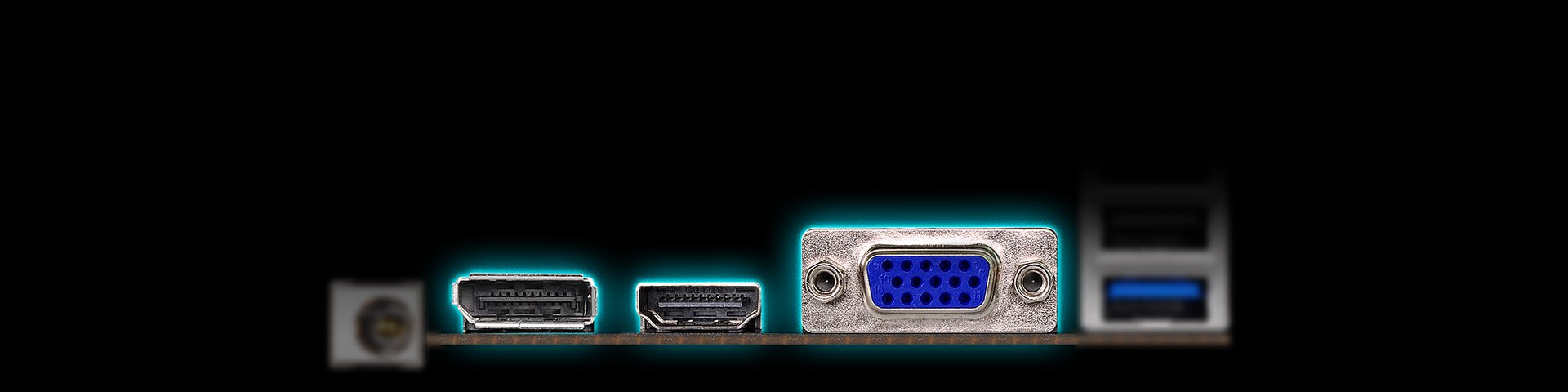
ASRock > DeskMini 310 Series

Amazon.co.jp: ASRock ベアボーン システムコンポーネント その他
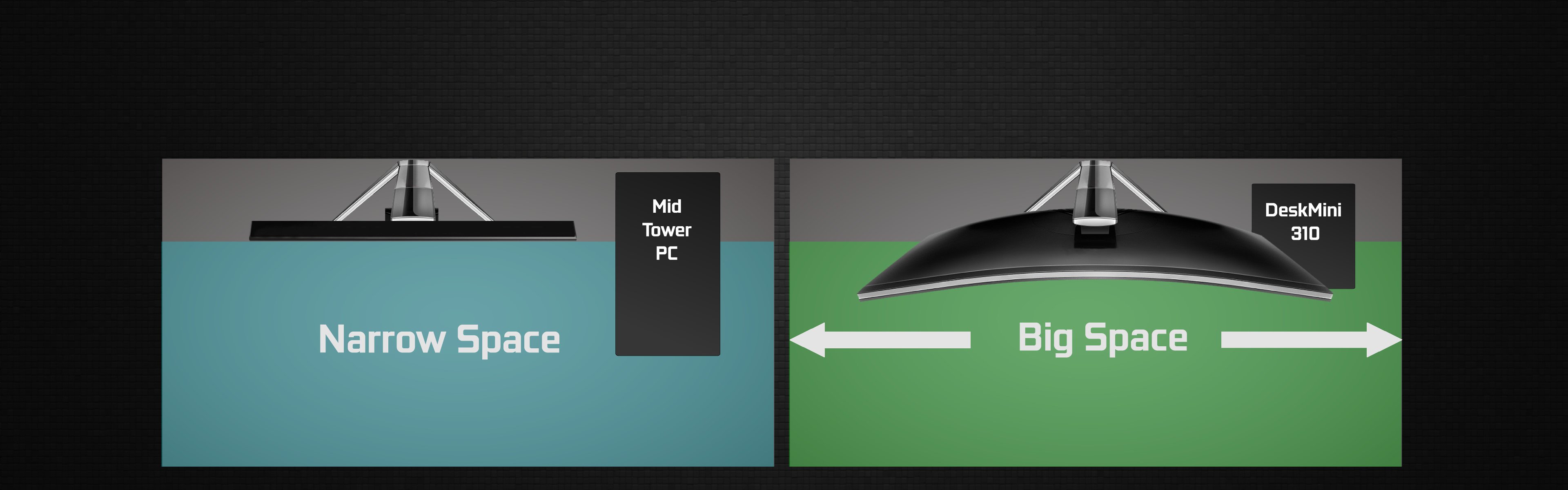
ASRock > DeskMini 310 Series

Amazon.co.jp: ASRock ベアボーン システムコンポーネント その他

ASRock DeskMini 300-

ASRock > DeskMini 310 Series
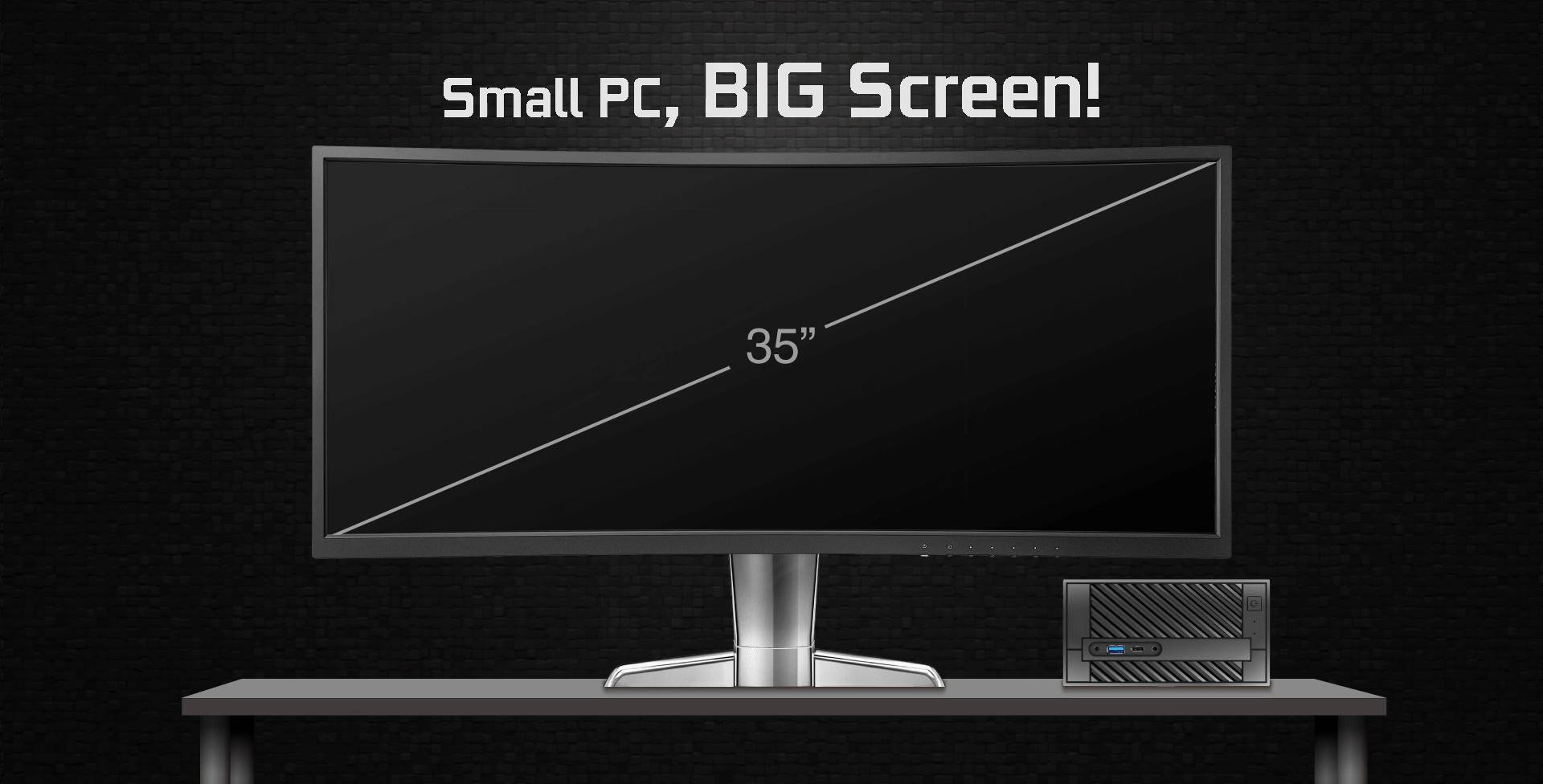
ASRock > DeskMini 310 Series

Amazon | ASRock Intel Socket LGA1200 Intel H470 ブラック ミニ

Amazon.com: Shuttle XPC Slim DH410S Mini Barebone PC Intel H410



商品の情報
メルカリ安心への取り組み
お金は事務局に支払われ、評価後に振り込まれます
出品者
スピード発送
この出品者は平均24時間以内に発送しています